When attackers compromise an asset in a network, that device usually is not their ultimate destination. To accomplish their goal, bad actors are likely to break into a low-level web server, email account, employee endpoint device, or some other starting location. They’ll then move laterally from this initial compromise through the network to reach their intended target. The initial compromise seldom causes severe damage. Thinking about this another way: if security teams can detect the lateral movement before the attackers reach their intended targets, they can prevent the attacker from successfully completing the mission.
But what exactly is lateral movement, and how does it work? In this blog, we’ll look at some of the most common types of lateral movement and identify ways by which we can detect and defend against this step in an attack.
Achieve Zero Trust Security
Zero trust is one approach to improving data center defenses. This approach calls for the inspection of every traffic flow within the data center. Zero trust divides the data center infrastructure into smaller security zones. Traffic between the zones is inspected to ensure it adheres to the security policies defined by the organization.
Overall, there are common ways by which a threat actor moves laterally. In one approach, the attacker uses tools designed to internally scan the network to gain information on other machines they may want to move to. Many of these enumeration tools do things like scanning for open ports that are listening and identifying machines that are suffering from unpatched vulnerabilities. Once the attacker has found a suitable target, they can take advantage of these weaknesses to move laterally to another asset.
Defending against lateral movement
It’s worth saying that lateral movement often manifests as anomalous network activity. It’s suspicious, for example, when a machine that talks regularly with only a select few computers begins scanning the entire network. The same is true if that machine attempts to connect to open ports, interact with credential services with which it doesn’t ordinarily maintain contact, or employ a username it’s never used before. The list goes on and on. What matters is that the computer is doing something out of the ordinary. Maybe there’s a legitimate reason for the activity, but maybe there’s not.
Examples like the ones above can give organizations a chance to detect lateral movement. They can turn to Active Directory, for example, to analyze log files for suspicious connections. Alternatively, they can use an endpoint detection and response (EDR) tool to detect if someone launches malicious code on a protected IT asset.
Prevent Lateral Movement with Granular Segmentation
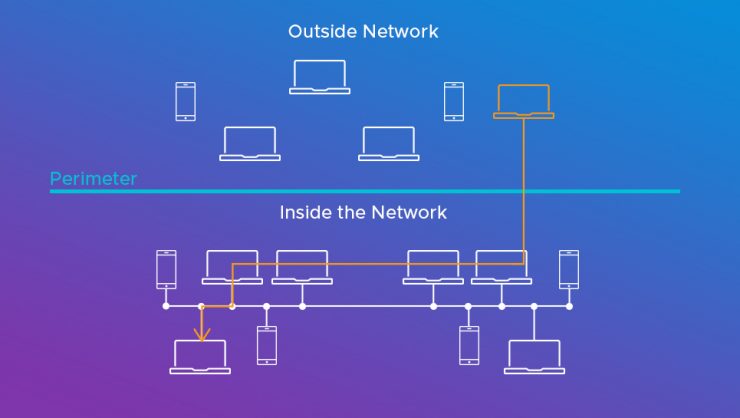
Micro-segmentation is an approach to dividing the data center infrastructure into small zones (see Figure 1). Effectively, micro-segmentation allows fine-grain control of traffic flows between every workload, allowing the administrator to protect all east-west communication. In other words, micro-segmentation helps achieve zero trust.
Secure critical workloads and environments with granular micro-segmentation protection, stateful Layer 7 controls, and dramatically simplified management.
Want to make your world a little smarter?
Get in contact with Christiaan Driessen and we will reach out to you.
Related Articles
Overstappen van VMware by Broadcom: noodzaak of kans?
30/10/2025
BPSOLUTIONS & Illumio: Samen voor Zero Trust Security
30/10/2025
Microsoft licenties veranderen: stap slim over en bespaar tot 13%
30/10/2025
Cyberaanval! Ben jij er klaar voor?
1/04/2025
Cybersecurity & Continuïteit: Isolated Recovery Environment as a Service
27/03/2025
Cybersecurity & Continuïteit: BaaS alleen is niet genoeg
25/03/2025
Cyberaanval? De impact is groter dan je denkt
23/03/2025








.png)